Getting Your Security DUCS in a Row (with Microsoft 365 Business Premium)
I was at a conference where I asked a group of IT professionals what they’re doing about security. I mentioned that we adopted Microsoft 365 Business Premium to protect our clients, and the general response was “you can’t trust Microsoft to protect Microsoft.” While I can empathize with that sentiment, the group didn’t have much beyond their favorite brand of antivirus as their security solution.
At Relion, we build on the following 4 pillars:
- Defender for Endpoint (Antivirus)
- Updates (All applications, not just Windows)
- Conditional Access (Pre-access health check)
- Security Baseline (Operating system hardening)
Defender for Endpoint
While I understand the negative sentiment towards Microsoft by the veterans of our community, today’s Microsoft ain’t your daddy’s Microsoft. Microsoft has gone through a remarkable transformation under Satya Nadella, and I think their Gartner ranking as the leader in Endpoint Protection is well deserved.
What undergirds Microsoft’s endpoint protection is the free Defender that comes with Windows. Defender already does a pretty good job at blocking common threats, but the Premium license supercharges it with EDR.
EDR collects behavioral patterns (telemetry) from all endpoints to a central log. Microsoft then uses machine learning to detect any anomalous behavior that may indicate attack patterns. EDR monitors the entire network, not just endpoints in isolation, so even if a hacker defeats the antivirus and gain a foothold, their lateral movements will be detected by EDR.
Updates
Patch Tuesday has been in the zeitgeist of network admins as long as our profession existed. There are well established tools like WSUS to help manage Windows Updates, but patching non-Microsoft products has always been a squishy proposition. Gaining visibility for critical vulnerabilities such as Log4j usually requires an expensive vulnerability scanner like Nessus.
Here again, Premium license comes to the rescue.
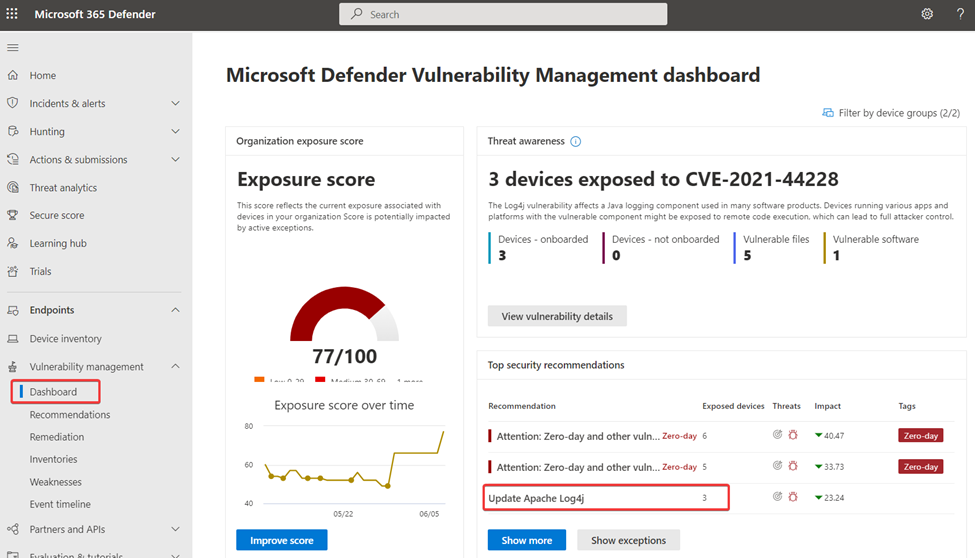
Using the Vulnerability Management dashboard, you gain visibility of all unpatched software in your network, Microsoft and otherwise. You can easily see in the example below that this network has three computers with unpatched Log4j. Hunting down critical vulnerabilities has never been easier.
Conditional Access
Traditionally when IT professionals talk about “security”, conversations centered around quality of antivirus, efficacy of patching, and hardening the network with a perimeter firewall. Now that we’re in a mobile, cloud-centric world, perimeter firewalls are simply inadequate to protect us while we’re out of the office. This is where Conditional Access steps in.
We use Conditional Access to perform two primary security checks:
- Identity verification – Are you who you say you are?
- Device compliance – Are you using a healthy, authorized device?
Identity verification is done through MFA.
Benefits of MFA are well documented, and service providers are now beginning to turn down new clients who refuse to adopt MFA. Resistance to installing a free authenticator app is akin to refusing to wear a seatbelt back in the day. It’s a minor inconvenience that people just need to get used to. Besides, no insurance company would cover someone who doesn’t believe in seatbelts and MFA is no different.
Device Compliance is a configurable set of conditions that are checked before access is granted. In practical terms, it could be as simple as allowing only company laptops access to Outlook, while blocking access from unregistered devices. You can see how this alone could prevent hackers from gaining access, since hacker aren’t issued company laptops!
There are other useful conditions to check, such as confirming that Defender is running and there are no active infections prior to granting access. This is the computer equivalent of checking your temperature before entering the building. If you’re not healthy, you’re not getting in.
Security Baseline
Would it surprise you to learn that Windows is insecure by design out of the box? Well, a more charitable statement would be that Windows is backward compatible out of the box. Luckily Endpoint Manager has pre-configured Security Baselines that tighten things right up.
In May 2022, the world was alerted of the Follina zero-day exploit, which allows an attacker to gain remote access to your computer through a Word document.
Despite all the hand-wringing about Microsoft not releasing a patch, Security Baseline stops the attack simply through Attack Surface Reduction, which does not require patching.
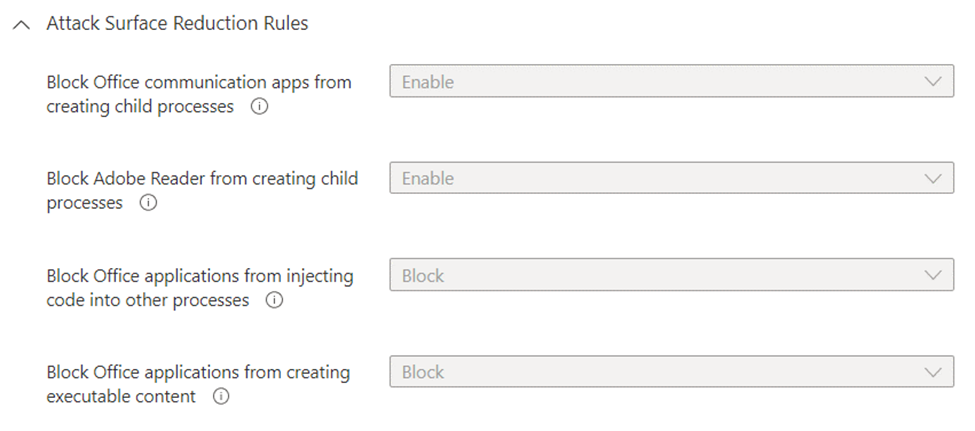
I can’t think of a good reason why you would allow Word or Excel to launch an executable. That may have been necessary in the good o’ days when VBA scripts were in vogue, but nowadays it’s downright dangerous. Same goes for Adobe Reader. Attacks through malicious PDF is such a common tactic, yet Acrobat allows child processes to be launched out of the box. 🤦♂️
Software makers do this in some kind of slavish devotion to backward compatibility. But what if you didn’t need it? What if Microsoft released a “secure” version of Windows that had everything locked down? That’s basically what Security Baseline gives you.
In Conclusion
There you have it. This is how Relion gets our security DUCS in a row. Rather than pinning all our hopes on having the “best” antivirus, we think good security design requires looking at the problem from all angles. Traditionally that meant buying a lot of expensive tools. Therefore, it’s surprising and amazing that Microsoft bundles everything you need in one Premium SKU. Like I said, this ain’t your daddy’s Microsoft.

Last Post: How Detailed Does HIPAA Policy and Procedures Need to Be?
